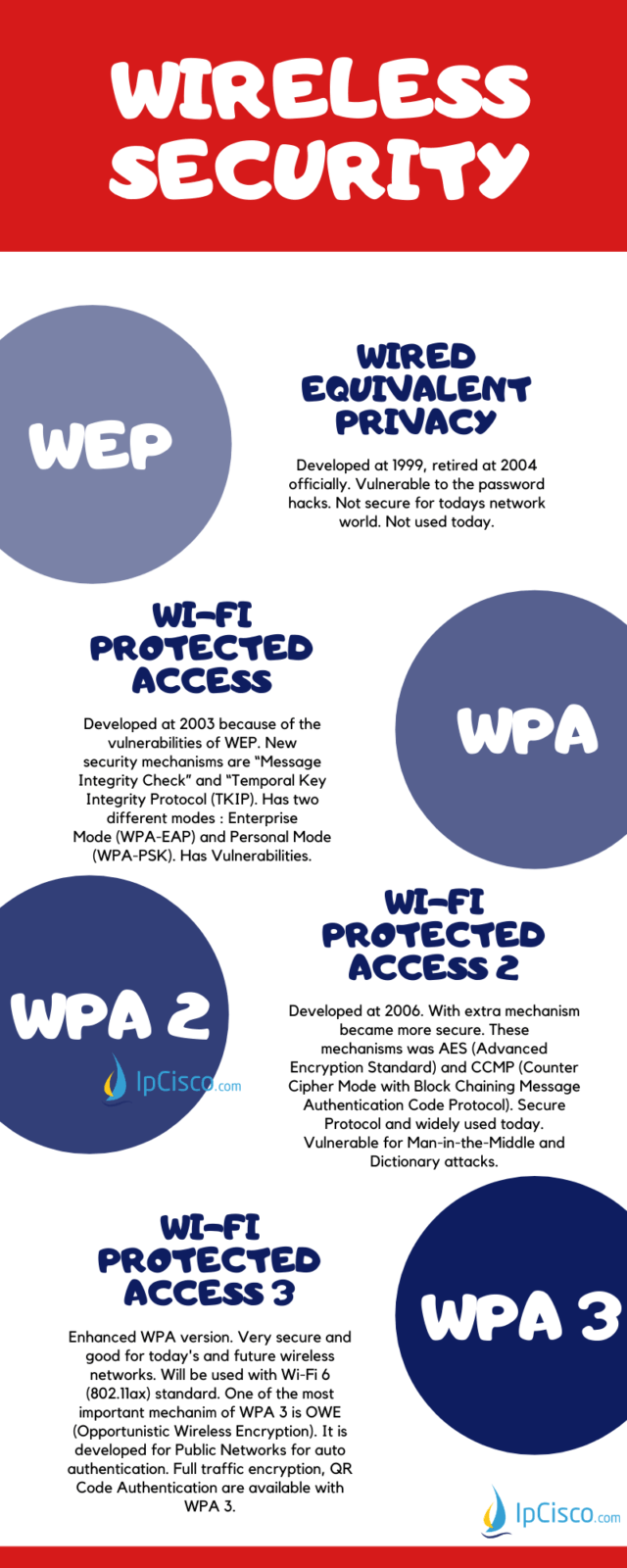
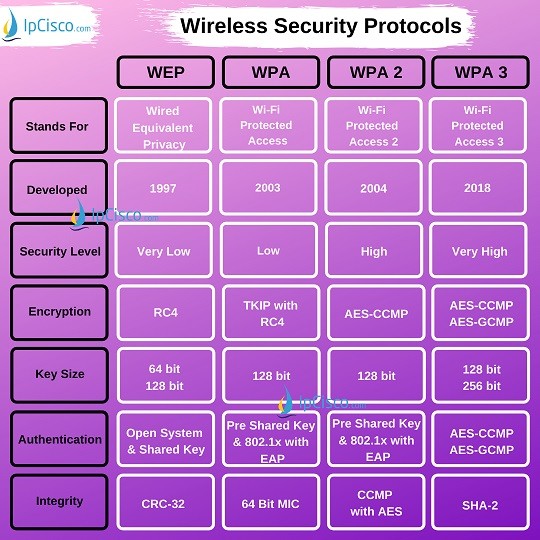
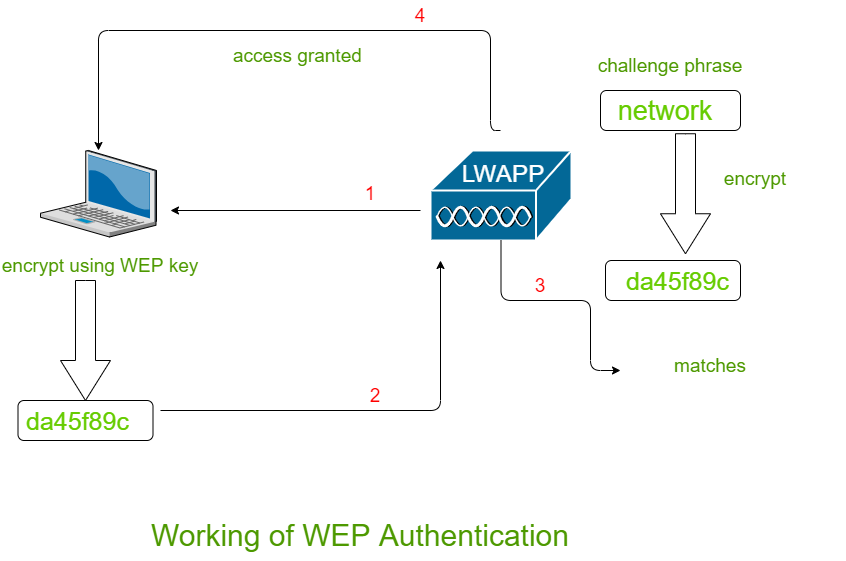
Wi-Fi Wireless Password Security Protocols | In this video we will see about wireless password security options. Understanding different type of security modes - WEP, WPA, WPA2, WPA3, WPS, and... | By

This wireless security protocol allows 192-bit minimum-strength security protocols and cryptographic tools to protect sensitive data, such as GCMP-256, HMAC-SHA284, and ECDSA using a 384-bit elliptic curve. Which is the wireless security